Tech
Zoom will enable waiting rooms by default to stop Zoombombing
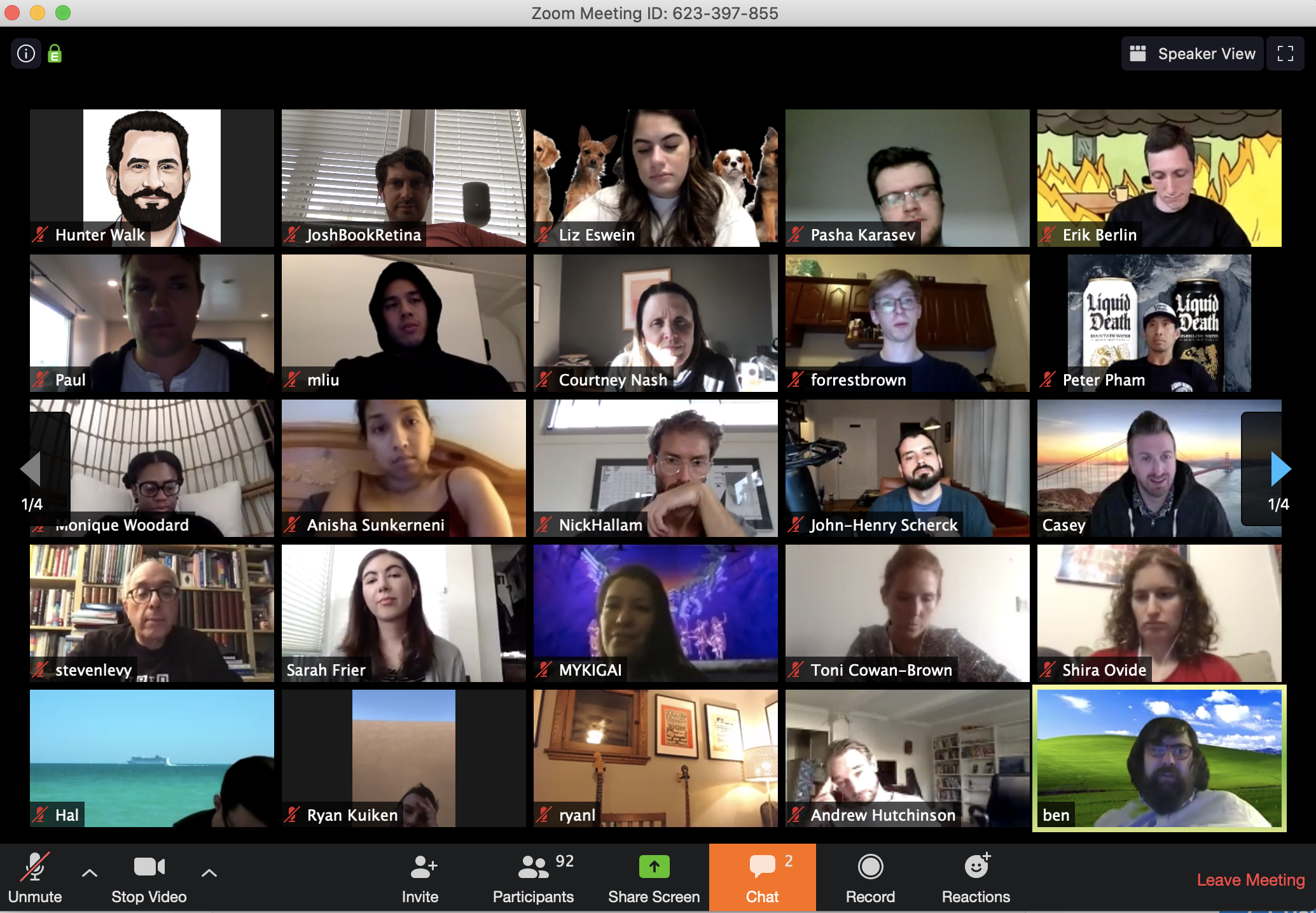
Zoom is making some drastic changes to prevent rampant abuse as trolls attack publicly shared video calls. Starting April 5th, it will require passwords to enter calls via Meeting ID, as these may be guessed or reused. Meanwhile, it will change virtual waiting rooms to be on by default so hosts have to manually admit attendees.
The changes could prevent “Zoombombing,” a term I coined two weeks ago to describe malicious actors entering Zoom calls and disrupting them by screensharing offensive imagery. New Zoombombing tactics have since emerged, like spamming the chat thread with terrible GIFs, using virtual backgrounds to spread hateful messages or just screaming profanities and slurs. Anonymous forums have now become breeding grounds for organized trolling efforts to raid calls.
Just imagine the most frightened look on all these people’s faces. That’s what happened when Zoombombers attacked the call.
The FBI has issued a warning about the Zoombombing problem after children’s online classes, Alcoholics Anonymous meetings and private business calls were invaded by trolls. Security researchers have revealed many ways that attackers can infiltrate a call.
The problems stem from Zoom being designed for trusted enterprise use cases rather than cocktail hours, yoga classes, roundtable discussions and classes. But with Zoom struggling to scale its infrastructure as its daily user count has shot up from 10 million to 200 million over the past month due to coronavirus shelter-in-place orders, it’s found itself caught off guard.
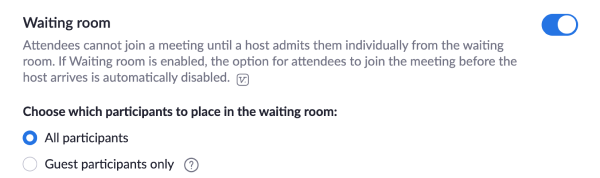
Zoom CEO Eric Yuan apologized for the security failures this week and vowed changes. But at the time, the company merely said it would default to making screensharing host-only and keeping waiting rooms on for its K-12 education users. Clearly it determined that wasn’t sufficient, so now waiting rooms are on by default for everyone.
Zoom communicated the changes to users via an email sent this afternoon that explains “we’ve chosen to enable passwords on your meetings and turn on Waiting Rooms by default as additional security enhancements to protect your privacy.”
The company also explained that “For meetings scheduled moving forward, the meeting password can be found in the invitation. For instant meetings, the password will be displayed in the Zoom client. The password can also be found in the meeting join URL.” Some other precautions users can take include disabling file transfer, screensharing or rejoining by removed attendees.

NEW YORK, NY – APRIL 18: Zoom founder Eric Yuan reacts at the Nasdaq opening bell ceremony on April 18, 2019 in New York City. The video-conferencing software company announced it’s IPO priced at $36 per share, at an estimated value of $9.2 billion. (Photo by Kena Betancur/Getty Images)
The shift could cause some hassle for users. Hosts will be distracted by having to approve attendees out of the waiting room while they’re trying to lead calls. Zoom recommends users resend invites with passwords attached for Meeting ID-based calls scheduled for after April 5th. Scrambling to find passwords could make people late to calls.
But that’s a reasonable price to pay to keep people from being scarred by Zoombombing attacks. The rash of trolling threatened to sour many people’s early experiences with the video chat platform just as it’s been having its breakout moment. A single call marred by disturbing pornography can leave a stronger impression than 100 peaceful ones with friends and colleagues. The old settings made sense when it was merely an enterprise product, but it needed to embrace its own change of identity as it becomes a fundamental utility for everyone.
Technologists will need to grow better at anticipating worst-case scenarios as their products go mainstream and are adapted to new use cases. Assuming everyone will have the best intentions ignores the reality of human nature. There’s always someone looking to generate a profit, score power or cause chaos from even the smallest opportunity. Building development teams that include skeptics and realists, rather than just visionary idealists, could keep ensure products get safeguarded from abuse before rather than after a scandal occurs.

Tech
Google Unveils AI-Powered Pixel 9 Lineup Ahead of Apple’s iPhone 16 Release
Google has launched its next generation of Pixel phones, setting the stage for a head-to-head competition with Apple as both tech giants aim to integrate more advanced artificial intelligence (AI) features into their flagship devices. The unveiling took place near Google’s Mountain View headquarters, marking an early debut for the Pixel 9 lineup, which is designed to showcase the latest advancements in AI technology.
The Pixel 9 series, although a minor player in global smartphone sales, is a crucial platform for Google to demonstrate the cutting-edge capabilities of its Android operating system. With AI at the core of its strategy, Google is positioning the Pixel 9 phones as vessels for the transformative potential of AI, a trend that is expected to revolutionize the way people interact with technology.
Rick Osterloh, Google’s senior vice president overseeing the Pixel phones, emphasized the company’s commitment to AI, stating, “We are obsessed with the idea that AI can make life easier and more productive for people.” This echoes the narrative Apple is likely to push when it unveils its iPhone 16, which is also expected to feature advanced AI capabilities.
The Pixel 9 lineup will be the first to fully integrate Google’s Gemini AI technology, designed to enhance user experience through more natural, conversational interactions. The Gemini assistant, which features 10 different human-like voices, can perform a wide array of tasks, particularly if users allow access to their emails and documents.
In an on-stage demonstration, the Gemini assistant showcased its ability to generate creative ideas and even analyze images, although it did experience some hiccups when asked to identify a concert poster for singer Sabrina Carpenter.
To support these AI-driven features, Google has equipped the Pixel 9 with a special chip that enables many AI processes to be handled directly on the device. This not only improves performance but also enhances user privacy and security by reducing the need to send data to remote servers.
Google’s aggressive push into AI with the Pixel 9 comes as Apple prepares to unveil its iPhone 16, which is expected to feature its own AI advancements. However, Google’s decision to offer a one-year free subscription to its advanced Gemini Assistant, valued at $240, may pressure Apple to reconsider any plans to charge for its AI services.
The standard Pixel 9 will be priced at $800, a $100 increase from last year, while the Pixel 9 Pro will range between $1,000 and $1,100, depending on the model. Google also announced the next iteration of its foldable Pixel phone, priced at $1,800.
In addition to the new Pixel phones, Google also revealed updates to its Pixel Watch and wireless earbuds, directly challenging Apple’s dominance in the wearable tech market. These products, like the Pixel 9, are designed to integrate seamlessly with Google’s AI-driven ecosystem.
Google’s event took place against the backdrop of a significant legal challenge, with a judge recently ruling that its search engine constitutes an illegal monopoly. This ruling could lead to further court proceedings that may force Google to make significant changes to its business practices, potentially impacting its Android software or other key components of its $2 trillion empire.
Despite these legal hurdles, Google is pressing forward with its vision of an AI-powered future, using its latest devices to showcase what it believes will be the next big leap in technology. As the battle for AI supremacy heats up, consumers can expect both Google and Apple to push the boundaries of what their devices can do, making the choice between them more compelling than ever.
News
Microsoft Outage Hits Payment Processors

When major payment processing systems have problems, the issues impact many critical systems that society depends on. In this article, we’ll explain the cause of the Microsoft outage and discuss the impact computer networking issues had on Canada. We’ll also examine whether or not Microsoft was at fault and what businesses can do to prevent further outages.
What Happened With the Microsoft Outage?
The outage with Microsoft’s Azure payment processor resulted from a buggy security update from an outside company, CrowdStrike. CrowdStrike offers information technology security services for many Microsoft Windows computers. The company’s software developers sent a new update out, but instead of patching up minor issues with the existing software, the code within conflicted with Windows and prevented computers from booting up. Users expecting to start their computers for a typical day were instead faced with the dreaded “Blue Screen of Death” error message.
So, how does this produce a problem and a payment processor issue? Many computers running payment processing, among many other kinds of software used for airlines, banks, retail, and other essential services, couldn’t start and were unable to let payments through. This is a catastrophic issue for companies that are heavily reliant upon the speed and ease of an electronic transaction.
In Canada, the outage impacted critical computer systems for air travel. Flights couldn’t be paid for and booked, which caused major problems for customers unable to make transactions while flights remained grounded. Travellers stuck waiting for flights to take off made their way over to the airports’ Starbucks and other vendors, only to discover unusually long lines due to payment issues. Even online gamblers looking to take their minds off the situation couldn’t take full advantage of one of the fastest payment options out there because of the outage.
Aside from payments, hospitals for major health systems had to use paper to complete important tasks like ordering lab work and getting meals to patients. Emergency dispatch lines were temporarily unable to function correctly while their computer systems were down.
How Was the Outage Fixed?
Thankfully, CrowdStrike fixed the problem on their end quickly, mostly via an additional reboot that allowed CrowdStrike to send over unflawed code. Unfortunately, for some business and private customers, rebooting wouldn’t be enough with command-line level adjustments needed for the operating system to run correctly.
The Good and Bad of Outages
First, we’re thankful that the outage was not caused by hackers accessing and stealing a mountain of personal data. A recent outage with an automotive software provider went on for much longer and ended much worse for software provider CDK, which likely paid an undisclosed sum north of $20 million to get data back and systems restored.
By some chance, Microsoft is reported to have experienced its own outage, and many information technology professionals blame Microsoft in part for their issues because of how their systems attempted to fix the problem by rebooting over and over again, though some of Microsoft’s PCs needed to warn users to make a change manually. Unfortunately, any computer that required manual intervention took longer to recover, as a knowledgeable person had to access each computer affected by the issue. In some cases, between dealing with several hours of backlogged tasks and slow recovery processes, some businesses took days, not hours, to get back online.
The outage brings up another major point in the cybersecurity and computer industry. CrowdStrike and Microsoft are both big companies in their respective fields. As a result, the effects of bad code spread much further than they could have if there were more competitors making security products or if there were more software companies making operating systems like Windows. While only 8 million computers were believed to be affected out of a much larger global network, those are essential computers for worldwide communication and payment processing. Perhaps companies should be putting their eggs in more than one basket?
The testing methods for the outage are unclear—did CrowdStrike test the routine software update enough to detect the potential for a major outage? Apparently not.
What Should Businesses Do Next?
Software like Microsoft Azure’s payment systems come from what information technology professionals call ‘the cloud.’ The software is remotely managed over the internet, meaning that the computer that runs the system is not physically present at the location. Unfortunately, this also means that an issue with the internet can take critical systems out of service.
Businesses ranging from major airlines and banks to mom-and-pop stores would be well served by backup systems at their locations. These don’t have to be as primitive as the old-fashioned credit-card carbon-copy slide, but there are options available with consistent service that don’t repeatedly rely on the same networks.
Conclusion
There were certainly challenging moments for Canadian businesses and emergency services during the CrowdStrike and Microsoft outage. As they scrambled to understand the problem and waited, albeit briefly, for issues to resolve, many companies learned the importance of having local and reliable backup for their computer systems.
Tech
New photos reveal more details about Google’s Pixel 9 Pro Fold

Google’s secret new line of Pixel 9 phones isn’t that big of a secret anymore. Taiwan’s National Communications Commission (NCC) released new photos of the phones including the Pixel 9 Pro Fold from almost every conceivable angle.
Android Authority found the photos in the NCC archives and uploaded galleries of each of the four phones including the Pixel 9, 9 Pro, 9 Pro XL and 9 Pro Fold. They reveal some interesting details about the new Pixel phones.
The charging rates will be a little faster than the last generation of Pixel phones: Taiwanese authorities measured 24.12W for the base model, 25.20W for the Pro and 32.67W for the 9 Pro XL. The Pixel 9 Pro Fold, however, was the slowest of all of them at 20.25W. These numbers don’t often match up perfectly with the advertised ratings, so expect Google to be promoting higher numbers at its event.
Speaking of chargers, it looks like Google needed a bigger charger to power its new phones. Photos included in the NCC leak show each phone will come with a wall charger that’s around 45W depending on which model you purchase. The charger’s plug moved from the middle to the top of the brick.
The latest photo dump also shows the 9 Pro Fold unfolded for the first time. Google has moved the selfie camera to the inside screen for a wider field of view. The 9 Pro Fold also has a slimmer top and bottom, a reduced fold crease on the display and a full 180 degree unfolding angle to make a screen that’s just over 250mm or just under 10 inches.
These photos are the latest in a very long list of leaks of Google Pixel 9 photos. The last Pixel 9 leak came down yesterday showing two prototype models of the base and XL models. Google might look into buying a new combination lock for the high school locker where they apparently keep all their unreleased gear.

-

 News17 hours ago
News17 hours agoNotre Dame suspends men’s swim team for one year after review finds NCAA gambling violations
-

 Business16 hours ago
Business16 hours agoJob Search Success Is More Likely With a Consultative Mindset
-

 News20 hours ago
News20 hours agoTenant advocate decries ruling that let B.C. landlord hike rent 27% after rates rose
-

 News15 hours ago
News15 hours agoThe Call for Change: Time Celebrities Get off the Money Train and Achieve for Their People
-

 News5 hours ago
News5 hours agoToronto man who fled to El Salvador charged with murder in wife’s 2004 death
-

 News17 hours ago
News17 hours agoWhitecaps FC Girls down Alianza in CONCACAF W Champions Cup playoff in El Salvador
-

 News6 hours ago
News6 hours agoStatistics Canada says manufacturing sales down 2.1% in June at $69.6B
-

 News15 hours ago
News15 hours agoSIU investigates after 19-year-old killed, another hurt in Innisfil police shooting





















